IPS and IT Security – Your most critically important business function!
The fourth industrial revolution is the current and developing environment in which disruptive technologies and trends such as the Internet of Things (IoT), robotics, virtual reality (VR) and artificial intelligence (AI) are changing the way we live and work.

For many years, the software industry has been producing unsecured software, due to customers and the market expecting high quality, chip software, very fast!
Some years ago, IPS recognized the critical importance of cybersecurity as a key business function and we established the IPS IAM (Identity and Access Management) project.
The whole enterprise software industry is moving forward in the cloud-based domain to support mobile devices, virtual and augmented reality, AI, IoT.
From a security point of view, this was a big challenge in developing the IPS IAM project.
The solution was to make an authentication service with the latest protocol support who supports SSO, Auth against single or multiple user stores (AD, Azure, Social network, IPS local DB).
There are many complex issues and factors to consider and this article will focus just on two areas, as follows:
Authentication => Who are you?
• Issues an Identity Token
• Identity system does not have intimate knowledge of application-specific authorization rules
• Do authorization as close as possible to the resource you are trying to protect
• IPS Identity Provider
Authorization => What are you authorized to do?
• Issues an Access Token
• A token can be re-used at several places
• Claims might have a different meaning for each consumer
• IPS Authorization Service
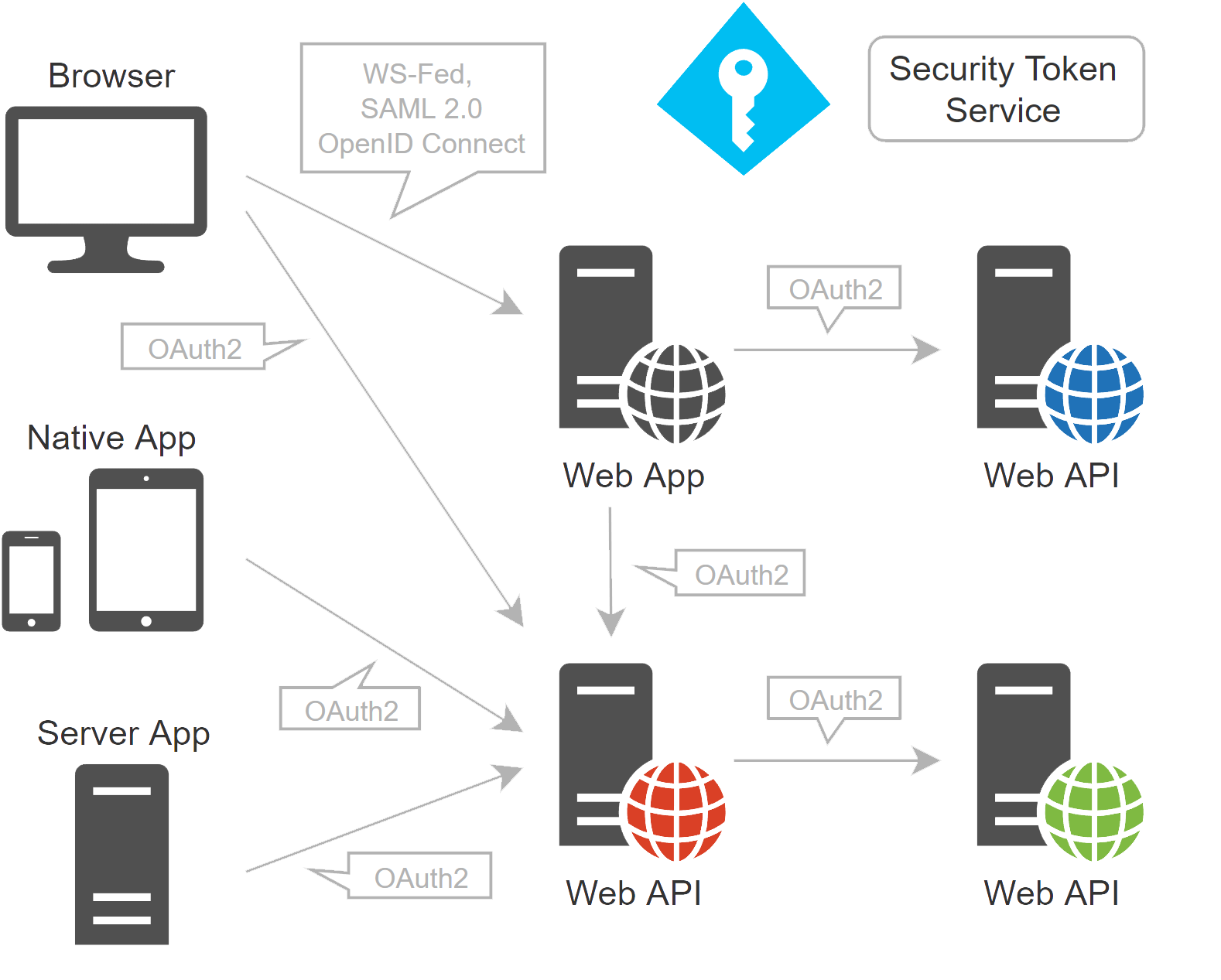
AUTHENTICATION IPS Identity Provider
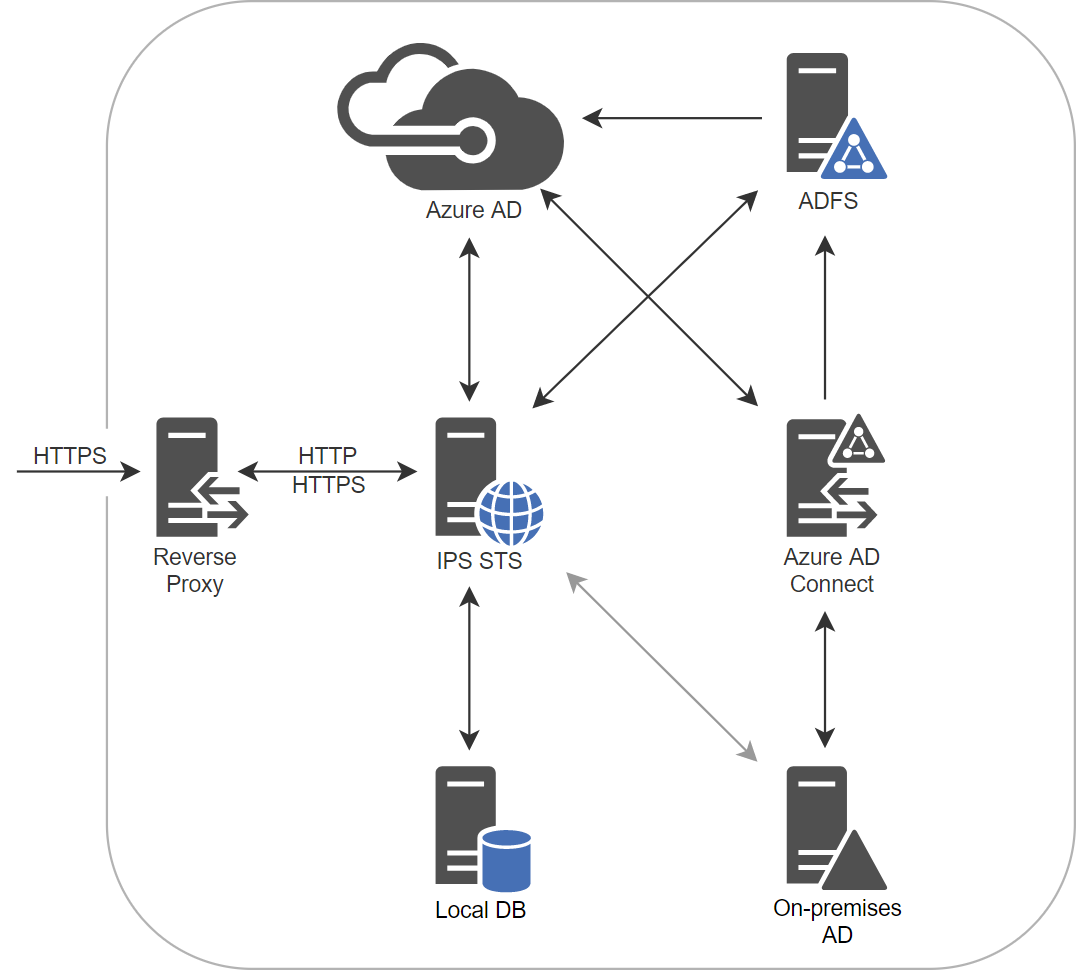
IPS Identity Provider, based on OIDC certified framework, is very flexible and easy to integrate.
• We can support authentication against multiple user stores, e.g. authentication proxy.
• We support legacy systems and protocols, so we can integrate with your existing security and expose modern OIDC Identity Provider, supported by the majority of companies, on the other end.
• All the other vendors with support for OIDC already have support for IPS Identity Provider.
Key features:
• Uses the latest security protocols for authentication and authorization (OpenID Connect and oAuth2).
• Single Sign-On (SSO)
• Supports multi-factor authentication
• Uses the latest encryption protocols to encrypt sensitive data in transit and on rest
• Identity Provider (IdP) and Federation Gateway (it can use other IdP, i.e. Active Directory)
• Supports authorization mapping from AD security groups so System Admins can maintain only one user store like AD
• Supports all major security standards and specifications (SAML 2.0, WS-Federation) so we can support legacy systems as well
• Supports Windows authentication
• Platform independent
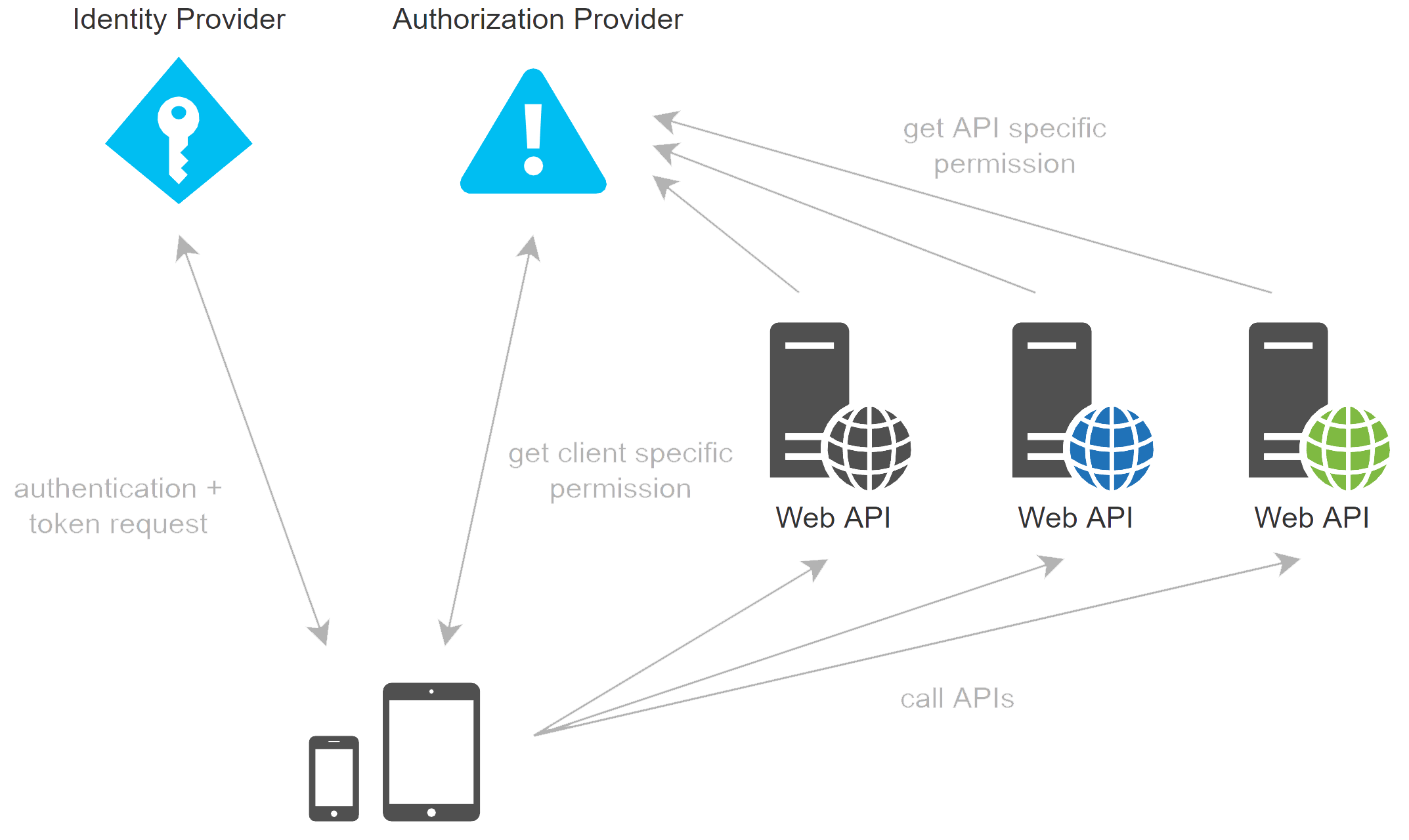
After successful authentication, the client app will contact the authorization server to get all permissions assigned to the logged-in user.
Web API receives a request from the client application and it also goes to the authorization server to get the list of permissions for that particular user and system.
Tokens can be re-used at several places and claims might have different meanings for each consumer.
Want to know more? – Please contact us via our Website Enquiry form!